
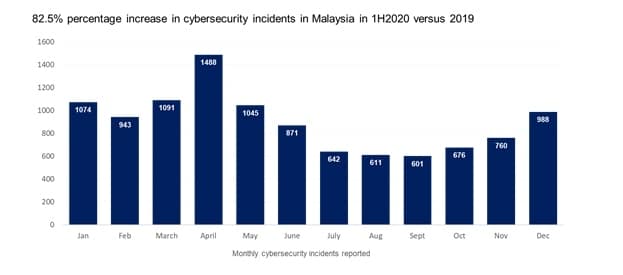
The COVID-19 crisis and the unprecedented acceleration towards digitalisation have caused companies worldwide to race onto digital platforms. As companies stepped onto digital means, they found loopholes and vulnerabilities in their digital systems. These issues are evident with the high number of cyber incidents reported, with more than 7,000 cases in Malaysia as of September 20201. Cyber fraud topped the list in Malaysia as the most common type of cyber-attack.
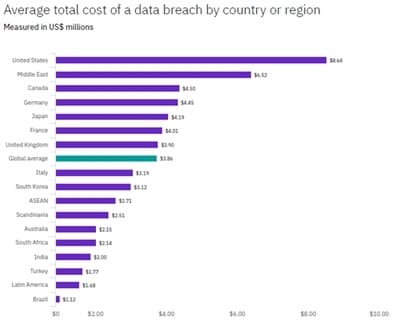
In its latest 2020 report, INTERPOL provided a sobering reality on the cyberthreat landscape confronting the Association of Southeast Asian Nations (ASEAN) countries. The first half of 2019 saw a rise in botnet infections, phishing scams, and ransomware, among others. Malaysia ranked among the top 3 countries in terms of mobile banking malware detections.
Alarmingly, it was revealed that Malaysian organisations cannot cope on their own to address the myriad cybersecurity threats. More than 70% of Malaysian organisations surveyed agreed that security is not their core expertise. Companies would rather engage a trusted partner for their security needs, according to IDC’s 2020 Asia/Pacific (excluding Japan) Enterprise Services Sourcing Survey

Against this backdrop, Malaysian enterprises that may not have the critical cybersecurity skills, technologies and cyber defence need to make urgent strategic choices. Hence, cybersecurity must be placed at the forefront of digital business initiatives and not as an afterthought. Cyber-attacks show a yearly upward trajectory. Leaders, however, tend to deny the possibility as it can affect their firm’s stature. This denial results in a spiral of incidents where businesses fail to defend themselves from cybersecurity strikes. As such, companies end up paying hefty fees to recover from the damages done. What firms could have protected earlier at a fraction of a cyber incident cost, now serves as a strong reminder of the importance of cybersecurity.
The detachment of cybersecurity from the business functions leads to a weak understanding of cyberattacks’ imminent threats on their business decisions. Organisations that do not comprehend cyber threats and their disastrous outcomes fail to quantify the risks across business decisions. Cyber strategies are often underfunded and low in resources as there is no intent to measure cyber threats and their influence. To counter this, leaders need to understand the key cybersecurity trends and align their priorities to strengthen their cybersecurity strategies.
Few considerations for the business leaders today:
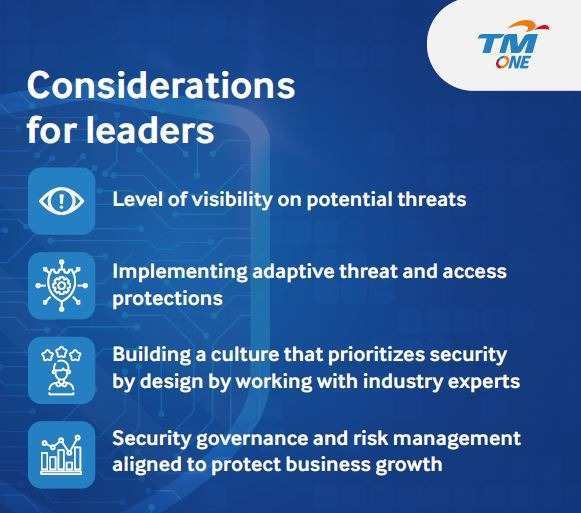


1. Realigning cybersecurity measures towards proactivity
Busines leaders needs to be more proactive in fighting cyber threats. The evidence regarding the commonplace of cyber-attacks on even large institutions suggests that big companies are not spared from such attacks. Cybersecurity incidents are traditionally dealt with in a reactive state of mind, leaving the organisation a step behind the attackers. A proactive stance allows the business leaders to securely guard their highly valued assets and build a robust digital infrastructure on all fronts.
2. Shifting the view on cybersecurity from a cost-based to ROI- and risk-based
Cybersecurity is often regarded as a compliance-driven, cost-based investment and a crisis manager – limiting its vast potential and value. These misconceptions can lead to a costly outcome. Having that traditional mindset ultimately disables important cross-functional insights from cybersecurity players, leaving the company vulnerable. Leaders need to view cybersecurity in terms of Return on Investment (ROI) and innovation-drivers. These drivers, in turn, enable the inclusivity of cyber insights into various functions of the business and tackles the problem of cybersecurity operating as a silo.
3. Integration and collaboration on cybersecurity
Business leaders require a ground-up rethinking of the culture surrounding IT and Security by encouraging integration and cooperation across functions and external experts. This move ensures a continuous knowledge transfer on cybersecurity, building high-skilled talents. Creating a culture that prioritises collaboration would allow cybersecurity functions to be innovation enablers and fully grasp the vital role cybersecurity plays in the organisation.
Traditionally, cyber strategies are mostly cost-based and referred to as an operational element of the business. By improving the integration and collaboration in the decision-making process, cyber budgets can be perceived as risk-measured and more strategically aligned with business targets. This process translates into a better understanding of the cyber threats that each business decision holds. As a result, business leaders can drastically improve their knowledge of the elements behind cyber strategies’ ROI. In the end, there is an allowance for better prioritisation and utilisation of the cybersecurity investment.
In Malaysia, generally we are still investing in conventional security technology, which is very much basic security, more reactive and only effective for damage control measures. It is time for us to seek a new proactive and more adaptive strategic approach to cybersecurity risk management that enables Active Cyber Defense (ACD) and cyber resiliency.
For businesses, this means real-time cyber defence services, resulting in valuable time and cost savings, avoid business disruption, providing peace of mind and regulatory compliance by preventing, mitigating or eliminating cybersecurity threats.
The Managed Security Services Provider or MSSP provide the bridge to balance the needs of cybersecurity to realise the value and benefits of cloud and digital services; to grow and protect the business and in return enable organisations to focus on their transformation journey, securely and comfortably.
TM One, the business solutions arm of Telekom Malaysia Berhad (TM) is ever ready to deliver digital security solution to businesses and organisations to safeguard their operations. TM One’s Cyber Defence Centre (CYDEC) is a fully managed security services that bring multiple benefits including global cyber threat intelligence services to protect brand and reputation, online fraud and business disruptions. CYDEC also offers real-time visibility with the Global Cybersecurity Operations Centre (G-CSOC) or a 24/7 monitoring of global Cyber Threat Intelligence (CTI) services with Active Cyber Defence (ACD) capabilities.
CYDEC also delivers numerous benefit to Malaysian enterprises and public sector institutions in building digital trust and cybersecurity resilience. This is done by managing the key five (5) key areas of risk - cybersecurity, compliance, privacy, ethics and social responsibility. These managed security services provide access to real-time, continuous, predictive cybersecurity, quickly and without complexity. With CYDEC, organisations can effortlessly ensure that in-house IT resources can remain focused on their business core matters.
Cyber threat is a huge risk to today’s world. In today’s digital era and ever-evolving technology standards, cybersecurity has quickly become a top concern and priority for individuals and companies worldwide. With this in mind, organisations are required to equip themselves to prepare for tight security measures and the best cybersecurity solutions to protect their vulnerability. It’s time to update your cybersecurity measures and get the security your business deserves. It is better to take preventive measures now than later recovering the after damages of cyberattacks. Always remember that an ounce of prevention is worth a pound of cure!
Reference
1 Reported based on General Incident Classifications, 2020, Malaysia Computer Emergency Response Team
2 Checkpoint Cybersecurity Report 2021, Checkpoint, 2021
3 Sophos The State of Cloud Security, Sophos, 2021
4 IoT Growth Demands Rethink of Long-Term Storage Strategies, IDC, 2020
5 2020 Unit 42 IoT Threat Report, Palo Alto Networks, 2020